As a cybersecurity enthusiast, I’ve always been fascinated by the power of Kali Linux. It’s like a Swiss Army knife for ethical hackers, armed with a plethora of tools for penetration testing and security assessments. But navigating the vast landscape of Kali Linux commands can feel daunting, even for experienced users.
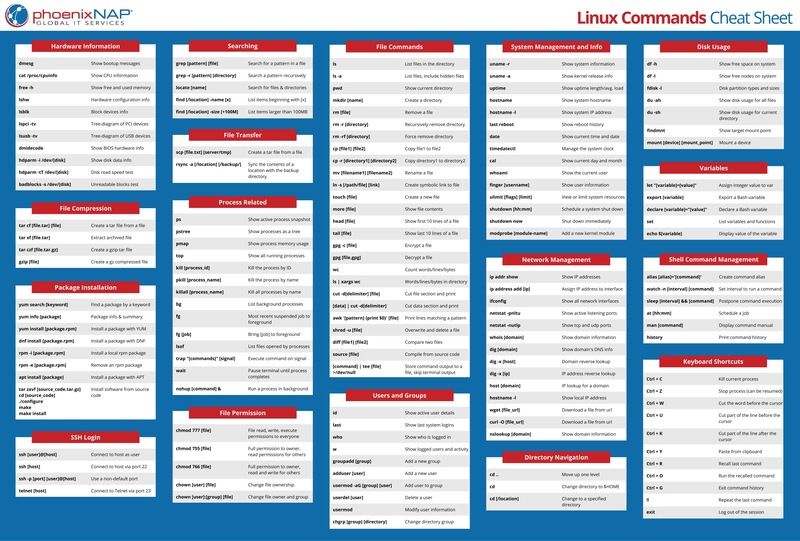
Image: phoenixnap.com
That’s where a comprehensive cheat sheet comes in handy. It acts like a trusty companion, providing quick access to essential commands for various tasks. Today, I’m excited to share my insights on why these cheat sheets are indispensable, dive into some essential commands, and even provide you with a downloadable PDF cheat sheet to get you started!
Why Use a Kali Linux Commands Cheat Sheet?
Imagine you’re in the middle of a penetration test, trying to identify vulnerabilities in a target system. You’re quickly switching between tools and need to remember intricate command lines. A cheat sheet becomes your lifeline, offering instant recall of commands for:
– **Network Reconnaissance:** Discovering hidden network devices, port scanning, and gathering information about target systems.
– **Vulnerability Scanning:** Identifying potential weaknesses in software and operating systems.
– **Exploitation:** Leveraging vulnerabilities for proof-of-concept attacks (always with ethical permission).
– **System Exploitation:** Gaining access to compromised systems and gathering sensitive data.
– **Post-Exploitation:** Maintaining access and collecting information after a successful exploit.
Unveiling Essential Kali Linux Commands
Let’s explore some key commands that are indispensable for any penetration tester:
1. Network Reconnaissance
- nmap: This versatile tool is a must-have for network scanning. It allows you to discover hosts, identify open ports, and gather information about services running on target systems.
- dnsrecon: Powerful DNS enumeration tool for domain reconnaissance, finding subdomains and hosts.
- whois: Retrieve information about domain names, including registrant details and contact information.

Image: bash-linux.com
2. Vulnerability Scanning
- openvas: Open-source vulnerability scanner that identifies and assesses potential weaknesses in systems.
- nessus: Widely-used vulnerability scanner with a robust database of known vulnerabilities.
- nikto: Specialized scanner for web servers, it checks for common vulnerabilities and misconfigurations.
3. System Exploitation
- metasploit-framework: Powerful framework for developing and executing exploits, providing a comprehensive toolkit for penetration testing.
- msfvenom: Generative tool for crafting custom payloads and exploits, offering flexibility for customization.
- exploitdb: Extensive database of exploits and vulnerable software, a valuable resource for discovering exploits.
4. Post-Exploitation
- wireshark: Powerful network packet analyzer for capturing and analyzing network traffic, providing in-depth insights into communication patterns.
- tcpdump: Command-line network packet analyzer for capturing and filtering network traffic.
- linux_priv_escalation: A collection of scripts and tools for escalating privileges and gaining administrative control over compromised systems.
Why Download a Kali Linux Commands Cheat Sheet PDF?
A PDF cheat sheet is your portable and easily accessible guide. It allows you to:
- Quick Reference: Instantly find the command you need without extensive searching.
- Offline Access: Use your cheat sheet even when you don’t have internet access.
- Printable: Keep a hard copy handy, perfect for those moments when you’re working on-the-go.
Expert Tips for Using Kali Linux Commands
Here are some tips based on my experience as a cybersecurity professional:
- Master the Basics: Start by understanding fundamental Linux commands like ls, cd, pwd, and mkdir.
- Experiment and Practice: The best way to learn is by doing. Set up a virtual machine with Kali Linux and practice using different commands.
- Read Documentation: Each tool and command has detailed documentation. Take the time to understand the intricacies of each tool.
- Stay Updated: Kali Linux is constantly evolving. Ensure your cheat sheet is up-to-date with the latest tools and commands.
FAQ
Q: What is the best way to learn Kali Linux commands?
A: The best way to learn Kali commands is through a combination of hands-on practice, referring to documentation, and using online resources like tutorials and cheat sheets.
Q: Should I memorize all Kali Linux commands?
A: Memorizing all commands isn’t essential. Instead, focus on understanding the most common commands and how to find the ones you need quickly using your cheat sheet.
Q: Is Kali Linux safe to use on my personal computer?
A: While Kali is designed for penetration testing, it’s generally safe to use on your personal computer if you understand its capabilities and only use it for ethical hacking.
Kali Linux Commands Cheat Sheet Pdf
Conclusion
A Kali Linux cheat sheet is an indispensable tool for any cybersecurity professional or enthusiast. It offers a quick reference guide to essential commands, making it easier to navigate and leverage the powerful arsenal of tools within Kali Linux. By understanding the basic commands and mastering the foundational tools, you’ll be well on your way to becoming a more skilled and effective penetration tester. So download your PDF cheat sheet today and embark on your cybersecurity journey!
Are you interested in learning more about Kali Linux commands?





